Attacking BGP through Looking Glasses
During the first-half of 2014, together with another researcher I performed an offensive security analisys focused on the core of the Internet: its global routing table.
We looked at real-life practices and tools deployed by network operators, identifying multiple attack venues and discovering several live incidents related to "looking-glass" softwares. The results described here have been peer-reviewed, presented at several security conferences, and also received a bug bounty.
Internet routing
The Internet is a network of networks, where each individual network is a so-called Autonomous System (AS). From an high level perspective, The Internet is composed by a large number of ASes which cooperate to exchange and carry data across their links.
Exterior gateway protocols such as the Border Gateway Protocol (BGP) are used to connect different ASes, and in this way the network of networks is created.
Routers are the devices responsible to connect the network nodes. In particular, backbone routers are hardware components of the Internet core infrastracture. They connect the ASes and are in charge of worldwide traffic routing.
Looking-glass software
When debugging BGP routing problems, engineers from a Network Operations Center (NOC) operators are often facing issues affecting only a specific set of ASes. Such problems are harder to debug due to the lack of a view on the remote routing table. For this reason, a new category of web-applications emerged in the ’90s to permit a restricted set of operations on routers and server owned by a different AS, by the large public, over the web. This kind of software is usually referred as "looking-glass" (LG), as it offers a local observation point to remote network engineers.
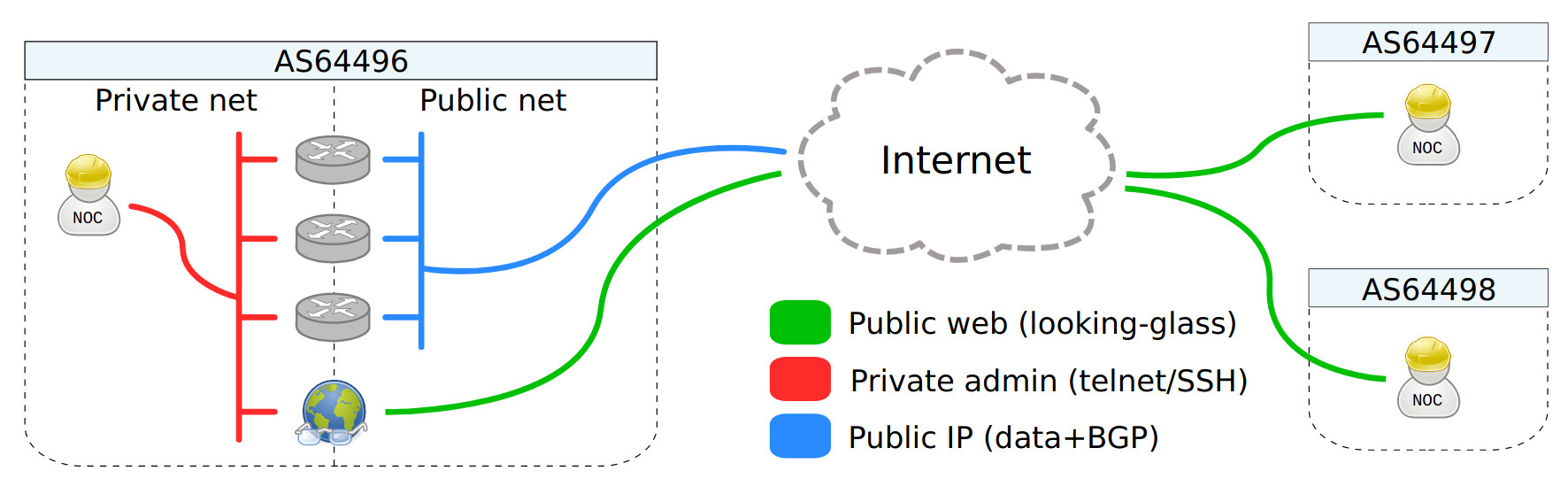
Looking-glasses are web scripts, usually implemented in Perl or PHP and directly connected to routers admin interfaces (i.e., telnet or SSH). These scripts are designed to relay textual commands from the web to the router and print back router's replies. They run on top of common Linux/Apache stacks, and sometimes provide additional utilities for latency and traceroute measurements.
Vulnerabilities
- MRLG4PHP
- CVE-2014-3927: Remote command injection to router's console via
argumentparameter
- CVE-2014-3927: Remote command injection to router's console via
- Cougar LG
- CVE-2014-3926: XSS in
<title>viaaddrparameter - CVE-2014-3928: Unsafe configuration file path/ACL
- CVE-2014-3929: Unsafe SSH keypairs path in default config
- CVE-2014-3926: XSS in
- Cistron LG
- CVE-2014-3930: Unsafe configuration file path/ACL
- MRLG
- CVE-2014-3931: Remote memory corruption in
fastping(SUID binary)
- CVE-2014-3931: Remote memory corruption in
Incidents
Some of these bugs (in particular 3927, 3928, 3929, 3930) have directly or indirectly resulted in exposed IPs, usernames, passwords, SSH private keys and remote command injection to router's console. Depending on the specific infrastructure setup, this may translate into an attacker having live access to routers CLI.
During the study, we detected around 45 incidents somehow related to above bugs, which we have already reported to concerned NOC contacts, whois contacts and national FSIRTs for further handling. Advanced private disclosure to concerned entities was performed on 2014/06/02.
A summary of the incidents we spotted in the wild is shown in the table below, with geographical distribution of impacted ASes.
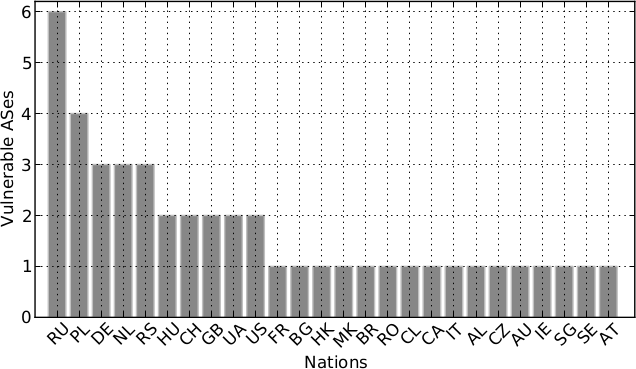
Summary of affected ASes, by category:
- Exposed configuration files: 28
- Remote command injection: 12
- Misconfigured CGI: 4
- Exposed SSH private keys: 3
Impact
A looking-glass is an often overlooked critical part of an operator infrastructure, as it sits at the border between the public web and restricted admin consoles. As such, an attack against this component may escalate from basic web scenarios to advanced worldwide networking threats.
Our results have been greatly summarized by one anonymous WOOT reviewer:
"Find old, open-source web apps that no auditor has ever touched before yet are used on extremely high value systems. Bloodbath ensues."
- Anonymous reviewer, WOOT '14
Post-exploitation scenarios are multiple and widely depend on actual network configurations. After abusing some of the above issues, an attacker may actually be capable of logging-in into backbone routers. Here, we just highlight some of the possible attacks that came to our mind:
- Gather and re-use credentials shared among several systems:
- Private SSH keys
- Login and passwords (we have found exposed root passwords too)
- Dump router configuration to:
- Bruteforce weak password
- Crack weak hashes, eg. on Cisco
- Discover and map internal/private/customer networks
- Map and DoS external control-plane endpoints, eg. BGP peers
- If needed, escalate privileges to admin console by:
- Cracking passwords
- Exploiting one of many local holes, eg. on Cisco and on Juniper
- Once admin, change router configuration to:
- Inject malicious BGP routes, eg. to hijack other prefixes or to saturate remote devices' tables
- Manipulate OSPF/ISIS/MPLS tables, eg. for rerouting or DoS purposes
- Set up your own BGP/GRE/MPLS/etc. channels, eg. for traffic mirroring
Reports
More detailed analysis of bugs, exploitation scenarios, incidents and impact can be found in the following proceedings:
- DEF CON 22 public presentation (slides)
- WOOT '14 research paper (slides, paper)
- HackerOne "The Internet" bug bounty (report)
Credits
Thanks to my colleague Mariano who worked on this with me, and to the whole security research team (S3) at Eurecom for support.